
FPGAs and Bitstream Encryption
FPGAs (programmable logic ICs) are an indispensable building block for many hihg-performance applications. Especially in security critical products not only hardware resources, but also the security features of a device are of major importance. The configuration data of common FPGAs are reprogrammed from an external memory during each startup. To avoid eavesdropping the leading FPGA suppliers, such as Xilinx and Altera, offer their own cryptographic solutions to protect the sensitive configuration data.
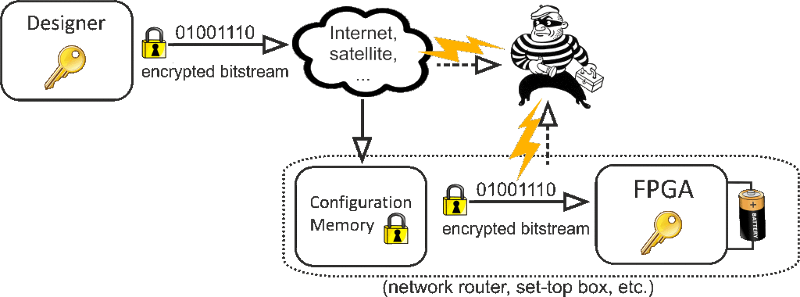
Our research results have shown, that the integrated bitstream encryption mechanisms of the device manufacturers can be defeated by means of side-channel attacks. Although the protection measures make use of modern cryptographic primitives, such as the AES and 3-DES, an attacker can still gain access to the sensitive technology know-how encoded within a bitstream.
Further more custom implementations of security features and cryptographic primitives in application-specific integrated circuits (ASICs), FPGAs or microcontrollers are vulnerable to side-channel analysis attacks unless state-of-the-art countermeasures have been employed to harden them.
Publications
Side-channel attacks on the bitstream encryption mechanism of Altera Stratix II: Facilitating black-box analysis using software reverse-engineering. Amir Moradi, David Oswald, Christof Paar, Pawel Swierczynski. Proceedings of the ACM/SIGDA international symposium on Field programmable gate arrays 2013. Monterey, California, USA. PDF
On the vulnerability of FPGA bitstream encryption against power analysis attacks: extracting keys from Xilinx Virtex-II FPGAs. Amir Moradi, Alessandro Barenghi, Timo Kasper, Christof Paar. Proceedings of the 18th ACM conference on Computer and communications security 2011. Chicago, Illinois, USA. PDF
Praktische Angriffe auf die Bitstromverschlüsselung von Xilinx FPGAs. Markus Kasper, Timo Kasper, Amir Moradi, Christof Paar. Datenschutz und Datensicherheit – DuD – Ausgabe 11/2011. PDF (German)
